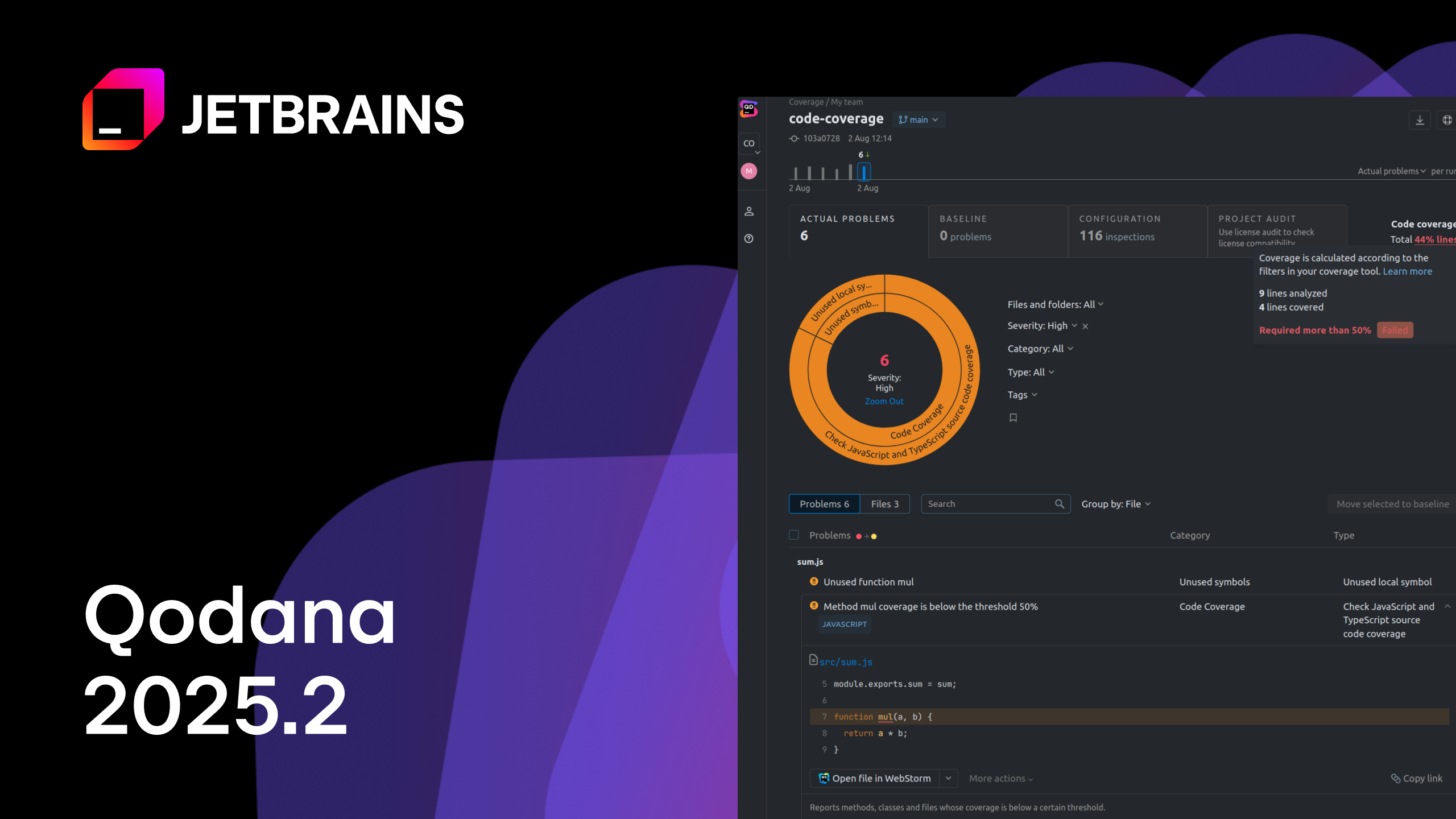
Qodana
The code quality platform for teams
Qodana 2024.2 Release: Enhanced Android Linter, Hard-coded Password Detection, and More
Get ready for new features and improvements with our latest Qodana 2024.2 release! This update introduces major enhancements that boost security, extend compatibility, and provide more convenience for development teams looking to increase code quality.
Here’s what’s new:
Table of Contents
View Qodana 2024.2 Documentation
Hardcoded password detection
Hardcoded passwords can be a critical security issue because, when exposed, attackers can use them to leak data and access sensitive information – especially in open-source or distributed applications. Passwords should be stored in a more secure environment. This is why we’ve introduced a new inspection to help you find these passwords in your code: HardcodedPasswords.
By default, the inspection reports variables with values matching built-in regex rules for hardcoded passwords. It currently supports JavaScript, TypeScript, Java, Kotlin, Groovy, PHP, Go, Python, C#, JSON, YAML, and XML.
How to detect hardcoded passwords, report variables with suspicious names, and implement your own regex rules
This inspection is enabled by default in Qodana. If you have a custom inspection profile, you should enable the inspection in your qodana.yaml profile as follows:
include: - name: "HardcodedPasswords"

Additionally, you can view reported variables with suspicious names, like token or password, and a constant string value. To enable this option, add the following configuration in qodana.yaml:
hardcodedPasswords: reportDefaultSuspiciousVariableNames: true
You can also implement your own regex rules to detect and report or ignore hardcoded variable values or names, offering you the opportunity to set up flexible custom rules.
Here’s an example of a custom rules configuration in qodana.yaml:
hardcodedPasswords:
# regex rules for variable values to report as hardcoded password
variableValues:
- "(?i)(xoxe-\d-[A-Z0-9]{146})"
- "perm:(?<clearSecret>[a-zA-Z=.0-9]{96}|[a-zA-Z=.0-9]{64})"
# regex rules for variable names to report as hardcoded password
variableNames:
- "youtrack"
# regex rules for variable values to ignore (not report) as hardcoded password
ignoreVariableValues:
- "do-not-report-this-value"
# regex rules for variable names to ignore (not report) as hardcoded password
ignoreVariableNames:
- "^(?=.*\bteamcity\b)(?=.*\bkey\b).*$"
New features and inspections for the Qodana-Android linter
With this release, our new qodana-android linter offers advanced features from the Qodana Ultimate plan, tailored specifically to Android projects. These include, but are not limited to, code coverage analysis and vulnerability checks. This enables you to get:
- Comprehensive inspections: The
qodana-androidlinter includes all inspections from the community version, plus additional inspections provided by the qodana-jvm linter. This ensures you can identify both Android-specific issues and language-related problems within your projects. - Enhanced analysis: By leveraging Qodana Ultimate features, you can perform deeper analysis on your Android projects, improving code quality (with the Code Coverage inspection) and security (with the Vulnerability Checker).
Get started with the qodana-android linter by specifying it in your qodana.yaml file:
linter: jetbrains/qodana-android:2024.2
Or use the following in the CLI:
--linter jetbrains/qodana-android:2024.2
Please note that inspections contained in external libraries and user-written inspections aren’t supported in this version.
With the qodana-android linter, you can now take your Android project analysis to the next level, ensuring that both Android-specific and general code quality issues are addressed.
Quick-fixes in Qodana for .NET – flagged, found, fixed!
The qodana-dotnet linter now supports quick-fixes, making it easier to improve your code automatically. You can choose between the cleanup and apply strategies to handle identified issues effectively. This means your team can enjoy:
- Automatic code improvement: Similar to other Qodana linters, quick-fixes in qodana-dotnet help streamline the process of fixing issues in your code where automatic corrections are possible.
- Flexible strategies: The linter supports both the cleanup and apply strategies, giving you control over how fixes are implemented.
How to use quick-fixes
To run the qodana-dotnet linter with the apply strategy, use the following command:
docker run \ -v $(pwd)/:/data/project/ \ -e QODANA_TOKEN="your Qodana Cloud Token" \ jetbrains/qodana-dotnet:2024.2 \ --apply-fixes # use --cleanup for cleanup strategy
Inspection changes and updates
- The
qodana-phplinter now includes JavaScript inspections by default, allowing analysis of PHP and JavaScript/TypeScript projects at the same time. - Android lint inspections are now integrated into the
qodana-android-communityand (new)qodana-androidlinters to address Android performance and security issues, improving performance and security and helping you find new bugs. - The
qodana-clanglinter is now available with different clang-compiler versions (15–18) so you can choose which version you want to use. The default linterqodana-clang:latestuses version 16 of the Clang compiler. To run it with a different version, you’ll need to specify it in the linter’s name:
linter: jetbrains/qodana-clang:2024.2-eap-clang<version> #(for example, jetbrains/qodana-clang:2024.2-eap-clang18)
Additionally, numerous inspection changes have been made to help identify potential coding errors, such as comparing an expression to itself, to help you make your code more robust.
What to do next
If you’re using the latest tag, you don’t need to do anything to enjoy the benefits of our new Qodana 2024.2 release. If not, please change from 2024.1 to 2024.2 to update. Users of GitHub Actions, Azure DevOps, and Circle CI can find the latest version of the extension here.
With these new enhancements, you have greater potential to substantially improve your coding experience with Qodana 2024.2. For further information, including detailed setup instructions for each feature, please refer to our official documentation. You can also stay up to date with Qodana by joining our communities on:
Subscribe to Qodana Blog updates