Qodana
The code quality platform for teams
Software Composition Analysis vs. Static Code Analysis: What’s the Difference?

Table of Contents
Modern software development relies on speed, reuse, and integration. Teams not only write their own code but also depend heavily on third-party libraries, frameworks, and open-source packages. To ensure security and quality in this environment, developers often turn to two different but complementary practices: software composition analysis (SCA) and static code analysis (SAST).
Although the names sound similar, these approaches have different purposes. Understanding the differences is key to building a good software quality and security strategy, improving developer experience and creating better products!
What is software composition analysis?
Brian Beckmann from Meta Reality Labs said “Compositionality is THE way to control complexity” which is relevant to SCA. Software composition analysis focuses on dependencies and third-party components in your codebase. Instead of analyzing the custom code written by your team, it scans for:
- Open-source libraries and frameworks included in your project
- Known vulnerabilities in those components, using databases like the National Vulnerability Database (NVD)
- License compliance issues, ensuring that dependencies don’t create legal or contractual risks
- Outdated or risky versions that could expose your application to exploits
SCA is most effective when used continuously in the development pipeline. It answers the question: “Is the software I’m building on top of safe and compliant?”
What is static code analysis?
Static code analysis, sometimes called SAST, looks at the custom code your team writes. Without executing the program, these tools scan source code or bytecode to find:
Code quality issues such as dead code, unused imports, and style violations, security vulnerabilities like SQL injection risks, improper input validation, or unsafe deserialization, Maintainability concerns such as overly complex methods, code duplication, or poor naming and performance pitfalls including inefficient loops or resource leaks.
Static code analysis integrates into IDEs and CI/CD pipelines, giving developers feedback early in the development process and can improve developer experience. It answers the question: “Is the code my team is writing safe, efficient, and maintainable?”
Software composition analysis vs. static code analysis: the differences
When comparing software composition analysis vs static code analysis, the distinction comes down to scope:

Other differences include:
| Aspect | Software Composition Analysis | Static code analysis |
| Scope | Dependancies, open-source packages, licenses | Custom application code |
| Main focus | Vulnerability detection and compliance | Code quality, security, maintainability |
| Timing | Often in CI/CD pipelines, also during dependancy management | During code (IDE) and CI/CD pipelines |
| Key risks | Known CVEs, risky libraries, licence violations | logic flaws, insecure coding practices, style issues |
How SCA and static code analysis work together
The most effective organizations don’t choose static code analysis vs software composition analysis, they use both. This is because both tools flag issues early, but they operate on very different parts of the software system. Each covers gaps the other leaves open:
- SCA ensures that external code is safe, up-to-date, and license-compliant.
- Static code analysis ensures that internal code meets quality and security standards.
- Combined, they create a holistic defense: identifying risks in your own work and in the ecosystem you rely on.
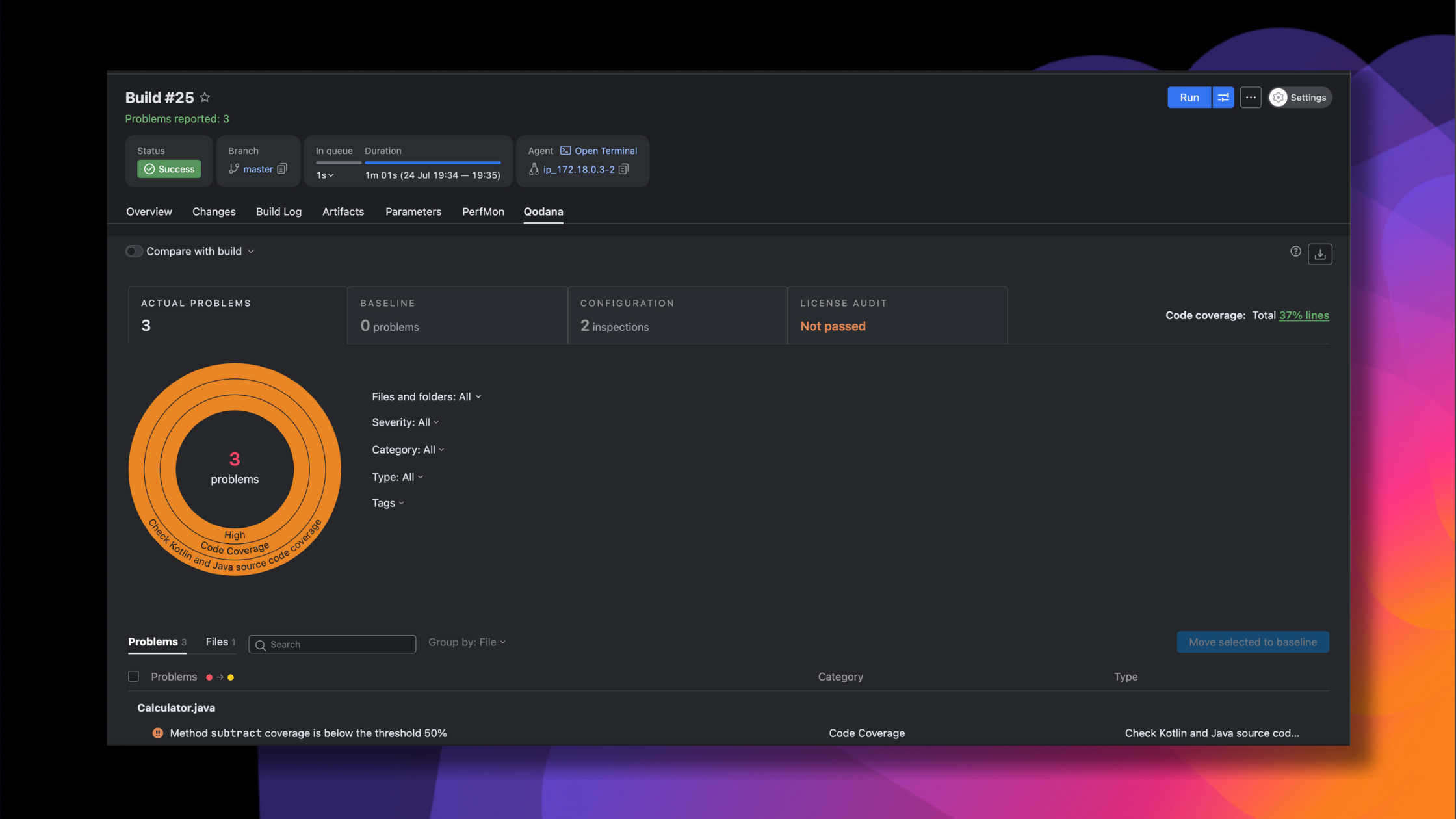
For example, Qodana integrates static code analysis with checks for vulnerabilities and license issues, giving teams a unified view of risks across both custom and third-party code.
Is Qodana a SCA or SAST?
Qodana is mostly a SAST (static application security testing) tool, also called static code analysis. It analyzes your own source code without running it, flagging:
- Code quality issues (dead code, unused imports, maintainability problems)
- Security vulnerabilities (unsafe input handling, SQL injection risks, etc.)
- Compliance concerns (license checks, potential policy violations)
That said, Qodana also includes some SCA-like capabilities, such as detecting license incompatibilities and known issues in dependencies. So it’s best described as a static code analysis platform with extended features that overlap into software composition analysis.
TL;DR
When comparing software composition analysis vs static code analysis, it is not an either/or choice. SCA focuses on external dependencies, while static code analysis focuses on internal code. Together, they improve overall code quality, reduce security risks, and make compliance more manageable.
By integrating both into your development workflow, you give your team the guardrails to build software that is not only functional, but secure, reliable, and sustainable.
Subscribe to Qodana Blog updates