IntelliJ IDEA
IntelliJ IDEA – the Leading IDE for Professional Development in Java and Kotlin
Enhanced Vulnerable API Detection in JetBrains IDEs and Qodana
At the start of the year, we announced a partnership with Mend.io to maximize code security in JetBrains tools. The partnership provided us with quality data about vulnerable and malicious packages, allowing our IDEs and Qodana to spot them for you in your projects.
Over the last few months, we have been working on integrating additional data about vulnerable APIs in open-source libraries, provided by the software composition analysis (SCA) data provider. That data has now been delivered to our Package Checker plugin, making it an even more effective tool for maintaining code security.
The Vulnerable API feature
The Package Checker plugin is powered by data from Mend.io about vulnerable APIs and provides code security analysis to detect the usage of vulnerable methods from open-source libraries.
Our team has recently been working on enriching Mend.io data to cover more public methods from open-source libraries by analyzing call graphs. This means that the plugin has more data at its disposal than ever before, covering more cases.
The plugin’s Vulnerable API feature works for various languages, including Java, Kotlin, C# (in Rider and ReSharper), JavaScript, TypeScript, and Python. Here’s how to make sure all the necessary inspections are enabled in the active inspection profile:
- First, open the IDE settings (⌘, on macOS or Ctrl+Alt+S on Windows/Linux) and go to Editor | Inspections.
- In the search bar, type “Vulnerable API” and you’ll see the list of related inspections (the final list depends on the plugins you have installed).
- Simply select the ones you need from the list.
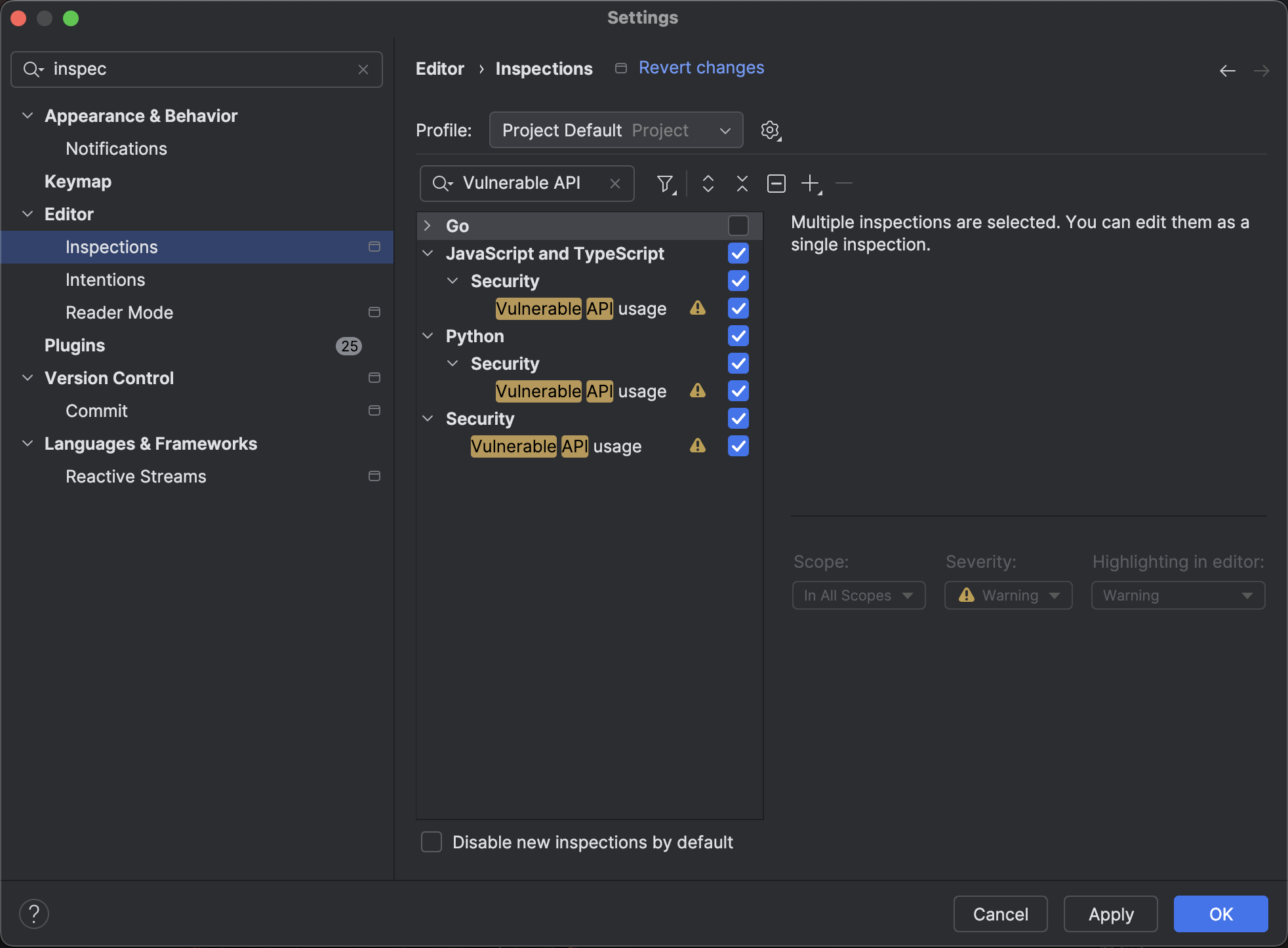
The Settings window
How to use it
The inspections provided by the Vulnerable API feature will highlight vulnerable methods from open-source libraries in your code. When you hover over the highlighted code, you’ll see a list of vulnerabilities found in a given API call. To address the problem, pull up the context actions (⌥⏎ on macOS or Alt+Enter on Windows/Linux) and select Go to file with declared dependency from the menu.
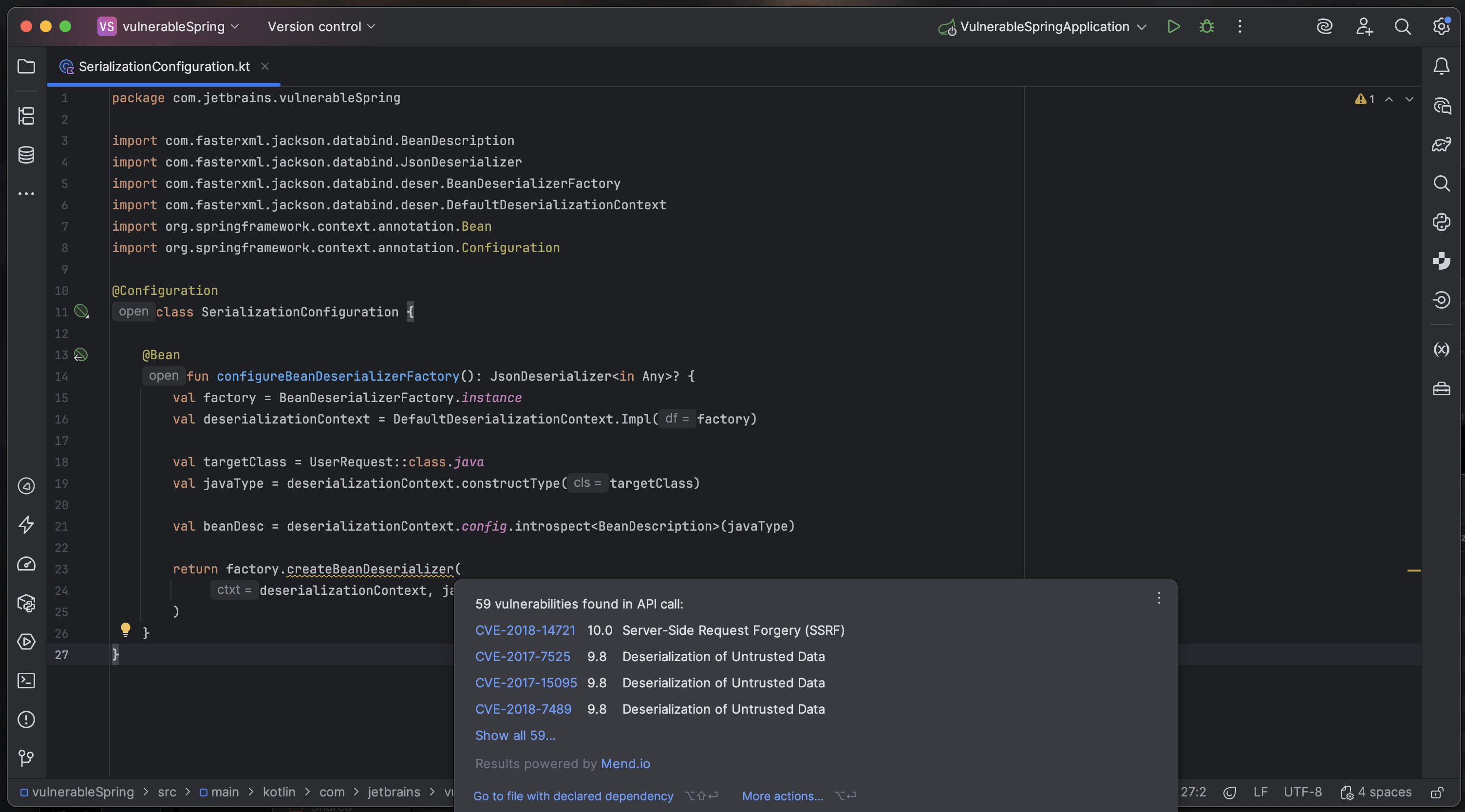
Vulnerable API highlighting
This will take you to the place in the build file where the dependency is declared. There, you can again use ⌥⏎ (on macOS) or Alt+Enter (on Windows/Linux) and select Update to unaffected version. The vulnerability list contains links to additional information in the Mend.io vulnerability database.
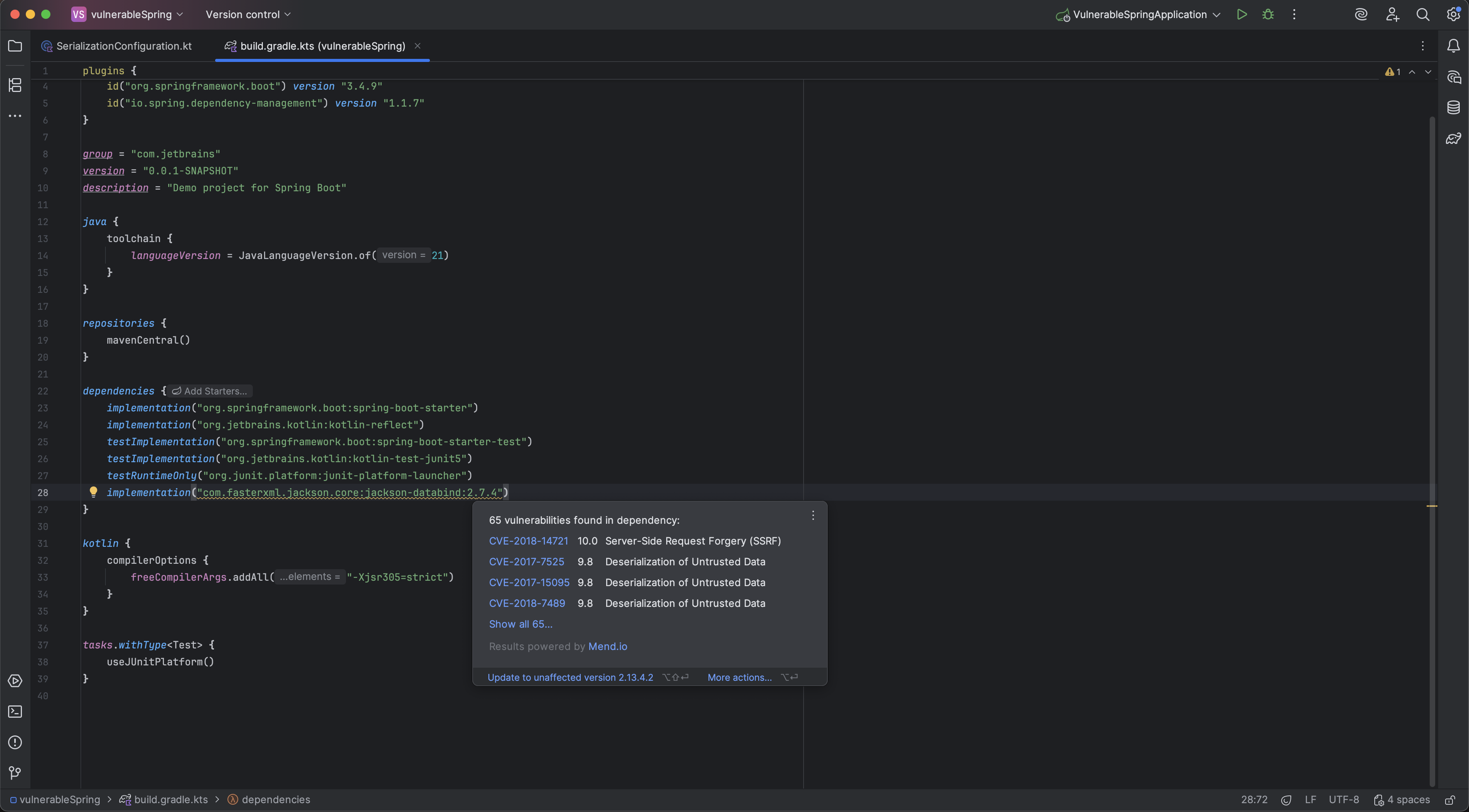
Vulnerable dependency highlighting
The Package Checker plugin also provides a way to see the list of vulnerabilities in a dedicated window inside the IDE without opening a browser. You can simply use the Show all… link. This will take you to the Vulnerable Dependencies window, which shows the overall state of the project and provides information about every detected vulnerable dependency.
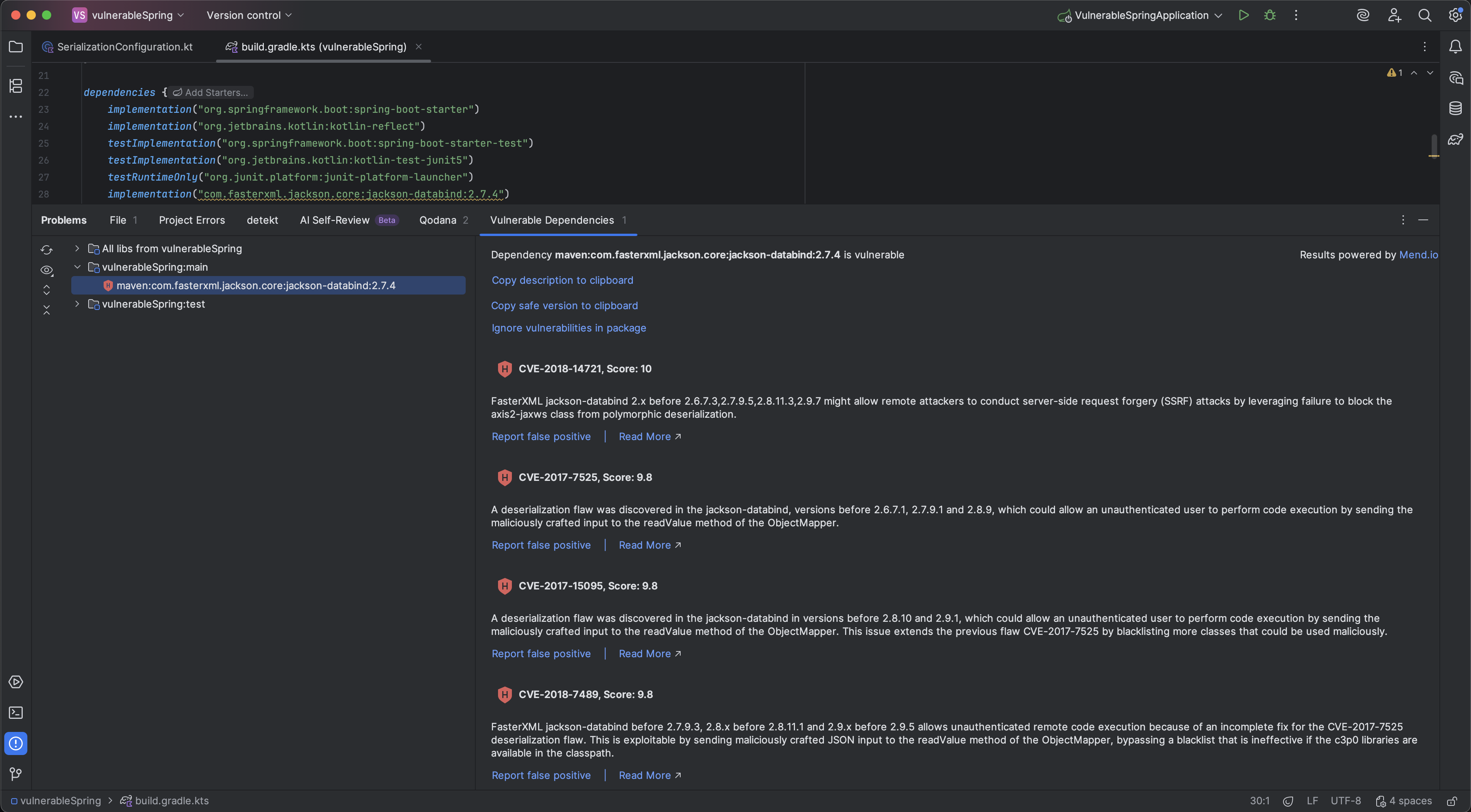
The Vulnerable Dependencies window
The Vulnerable API and Vulnerable Dependencies features are available in Qodana and can be used in CI/CD or security assessment processes.
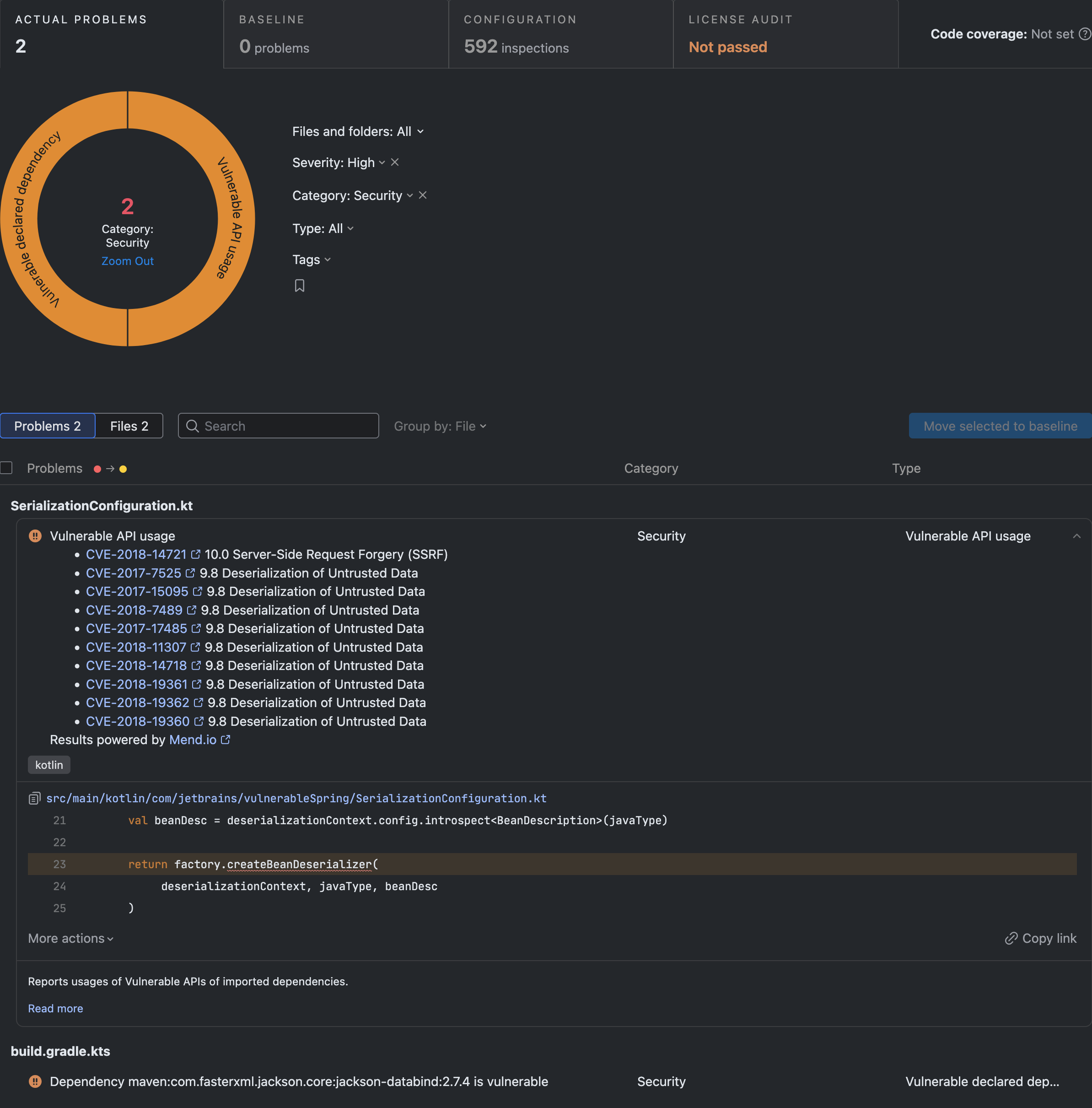
Vulnerable API feature in Qodana
Looking ahead
These improvements strengthen the existing code security features in JetBrains IDEs and Qodana by providing enhanced vulnerability detection capabilities. Update your IDE to the latest version and enable the Vulnerable API inspections to identify security risks in your codebase.
You can learn more about the Package Checker plugin from its page on JetBrains Marketplace, and you can find more information about how to use it in the documentation. For more details about our collaboration with Mend.io, check out this blog post.
Subscribe to IntelliJ IDEA Blog updates








