TeamCity
Powerful CI/CD for DevOps-centric teams
Configuration as Code for TeamCity Using Terraform
Addressing the DevOps challenge
In DevOps, development and infrastructure tasks are split. Developers and build engineers handle project configuration and scripting, while DevOps engineers on the infrastructure side manage things like TeamCity instances, database maintenance, and permissions.
Although the Kotlin DSL can address CI/CD needs at the project level, it lacks system administration capabilities. It is incapable of setting universal server configurations and managing users, which poses challenges for DevOps engineers, especially those from a systems administration background.
To overcome this, TeamCity has introduced the Terraform Provider for TeamCity on the basis of this widely adopted infrastructure provisioning tool. The Terraform Provider uses a language familiar to DevOps professionals and streamlines global server setup, user management, permissions, and project initiation.
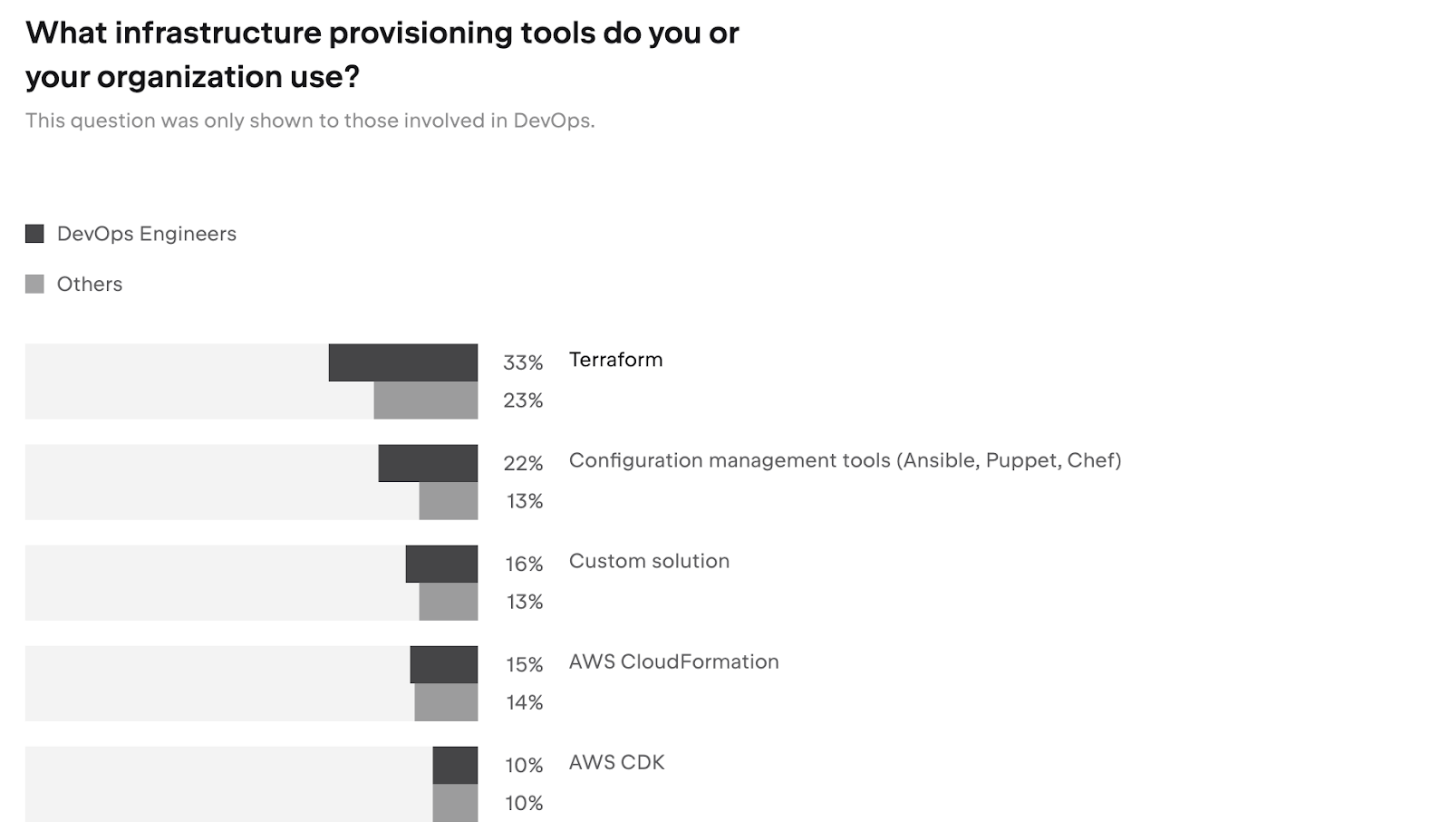
Source: Developer Ecosystem Report 2023
Terraform Provider in action: Setting up OAuth for GitHub accounts
Let’s see how we can use the new Terraform Provider for TeamCity. In the first example, we’ll set up OAuth for GitHub accounts. Here, we need to change the server URL and then add a GitHub App authentication model.


In Terraform, we can describe our web forms as a set of resources. For the global settings, we can change the server URL. All of the other settings are left as default.

Then, we add a module for authentication as shown below.

We also need to add a connection with our custom GitHub App into our root project.

We can also configure SMTP settings for notifications, add license keys, and set up cleaning.
Terraform is a command line tool. Here, we can type in terraform apply, and it will evaluate our configuration files and declare which changes will be made in our infrastructure.

Once the changes are applied, we can log in to TeamCity with a new external account.
Creating accounts and granting permissions in advance
In TeamCity, you can create custom roles and grant only certain permissions to certain roles, following the principle of least privilege. Let’s see how to do so using Terraform Provider.
Let’s create a new custom role, a project, and a new group, and assign project permissions to the group.

When the user connects to TeamCity for the first time, they’ll immediately have access to their projects and custom permissions.
The project that we created is empty. However, when you start developing a new product or microservice, it’s great to provide the team with a working example. Here, we have a repo in GitHub with a basic Kotlin DSL script.

Now, let’s register it in TeamCity. We’ll create a project, and within it, register an SSH key and create a VCS root using SSH authentication.

We can also enable versioned settings there to ensure our Kotlin DSL script is applied.

Managing GitHub resources via Terraform
Terraform doesn’t just refer to GitHub resources but actually manages them. To demonstrate how this feature works, let’s create a new repo by cloning it from a template.
In the code, we declare a new GitHub repository and refer to our template as a base for cloning.
This integration can also work the other way around. Namely, Terraform can also reflect changes in your actual infrastructure. Now, let’s see how we can create a repo manually.

Here, we’ve listed all of the repos in their organization and ensured that each of them has a corresponding set of TeamCity resources.

As we can see, Terraform was able to find a new repo that we recently created.

We can also add a set of TeamCity objects, and they will appear automatically in the corresponding TeamCity project.
Importing existing resources
For those who have been working with TeamCity for a while, there is a way to import existing configurations and settings into Terraform without recreating everything from scratch. Here’s an example of how we can customize existing settings.
Here, we’ve specified the ID of a TeamCity object and the ID of a resultant Terraform resource:

Now, we can tell Terraform to go into an actual TeamCity instance, read its state, and generate configuration files.

Terraform will then fetch the list of permissions from TeamCity.

We can then go ahead and add a new permission in Terraform. It will then automatically appear in TeamCity.
Learn more about Terraform Provider for TeamCity
You can find the Terraform Provider for TeamCity in the HashiCorp Terraform registry. Please refer to the documentation for more resources and details.
Also, make sure to check out the project’s GitHub repository.
If you have any questions, feel free to reach out to us – we’ll be happy to help.
Subscribe to TeamCity Blog updates







