TeamCity
Powerful CI/CD for DevOps-centric teams
The official TeamCity CloudFormation template
⚠️ Please note that the official CloudFormation template for TeamCity has been deprecated and is no longer supported.
As you might have noticed, there was recently an option added to the Get TeamCity page of our website: AWS. This lets you run TeamCity in AWS using the official CloudFormation template.

In this post, we will go over what’s under the hood of the template, and why it may save you some time and effort.
Usually, installing TeamCity on top of AWS is quite a time-consuming task.
It requires the following steps:
- Setting up an external database,
- Configuring the EC2 instance to run a TeamCity server,
- Configuring it to then connect to the database,
- Installing the TeamCity server,
- Installing a TeamCity agent.
And then making the whole installation secure requires even more effort.
We have tried to ease this process and created an official CloudFormation template to run the TeamCity stack in AWS. Using this template lets you run all the above steps with just a single click. And should you decide to destroy the stack, CloudFormation also provides a super simple way to do it with just one click.
The template is located in the S3 bucket. The stack can be launched via the ‘Run on AWS’ button available on the TeamCity site.
The template provides several parameters:

It takes about 15 minutes for the template to deploy the whole stack, the most time-consuming task being the RDS Database instance roll up. Once the deployment is ready, you will see the TeamCity server endpoint in the Output section which points you to your TeamCity installation.
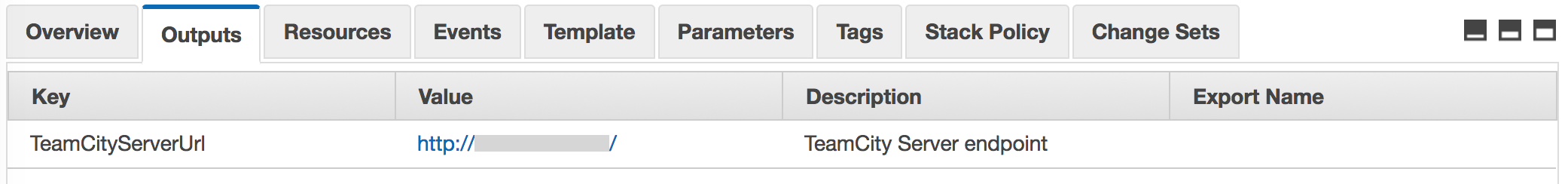
Just generate the root account and it’s ready to use.
So what is under the hood?
The TeamCity server runs on an EC2 instance with CoreOS Container Linux. The default agent runs as a separate container on the same instance. The external database is provided by an RDS MySQL instance. We decided not to introduce a custom AMI with TeamCity. Instead, we use the official Docker images with the TeamCity server and build agent.
The server and the database are placed in their own VPC which is completely secure. The DB allows only internal connections within the VPC. It’s only possible to connect to the Server via HTTP(s) or SSH.
How the server is running
There are several systemd services that prepare the LVM on the EBS volume to persist your data, create the file system, and run the latest official TeamCity Server and TeamCity Build Agent from the DockerHub images. Those services are linked to each other and roll the whole system back after an instance reboot or failure.
To connect to the server’s console, you need to use your instance key:ssh -i instance-key.pem core@[server IP]
To see the logs, just run the docker logs command for the desired container.
Once you have TeamCity up and running, there are a few more steps to consider:
- Use the EC2 integration to run and connect build agents to your server, and
- Configure TeamCity to use the S3 bucket as external artifact storage.
Happy building with TeamCity on AWS!
Subscribe to TeamCity Blog updates






