TeamCity
Powerful CI/CD for DevOps-centric teams
SAST vs DAST: Differences And When to Use
Anyone working in the software development field knows cybersecurity is a threat you cannot afford to downplay. A cyberattack on a product or service you’ve created carries a risk of serious financial and reputational damage, as well as regulatory penalties, depending on the industry and jurisdiction.
Defending your software against cyberattacks means addressing security at every stage of the software development lifecycle (SDLC) – from design and development to testing and production monitoring.
Two techniques to help you do this are Static Application Security Testing (SAST) and Dynamic Application Security Testing (DAST). While they may sound similar, SAST and DAST are different testing styles. Teams use the approaches at different points in the SDLC to detect different types of vulnerabilities.
Compare the differences between SAST vs DAST and understand the benefits each offers, and why it’s a good idea to use both techniques as part of your CI/CD process.
In this article:
- What are SAST and DAST?
- SAST vs DAST: key differences
- When to use SAST, DAST, or both
- SAST vs DAST tool comparison
- How to implement SAST and DAST effectively
- How TeamCity can help
What are SAST and DAST?
SAST
SAST is a type of automated security testing that examines your source code or binaries for known vulnerabilities. SAST tools allow you to verify you haven’t introduced any security flaws with your latest changes, by checking your code line by line.
As SAST doesn’t require a build, you can run these tests as part of your merge or pre-commit checks and get feedback early on in the development process. When a SAST tool identifies a vulnerability in your code, it also reports the relevant line of code so you can go straight to the source of the issue.
You can find out more, including key considerations and best practices, in our complete guide to SAST.
DAST
DAST runs a series of automated security tests on a deployed web application. DAST tools start by crawling your application to identify all possible endpoints, then systematically analyze the responses and simulate attacks.
The results are typically reported with suggested remediation steps, but you’ll need to identify the relevant section of code yourself.
When comparing SAST vs DAST, DAST can only provide feedback at a later point in the SDLC, once you’ve built and deployed your software to a testing environment. However, this means you can use DAST to test how your application interacts with other systems and services.
Check out our guide to DAST to learn more about how the technique works, as well as best practices to help you get the most out of it.
SAST vs DAST: key differences
SAST and DAST are different styles of automated testing. There is some overlap in the types of vulnerabilities that each approach detects, but the differences in methodology mean these techniques are complementary, not competing.
Let’s look at the differences in more detail.
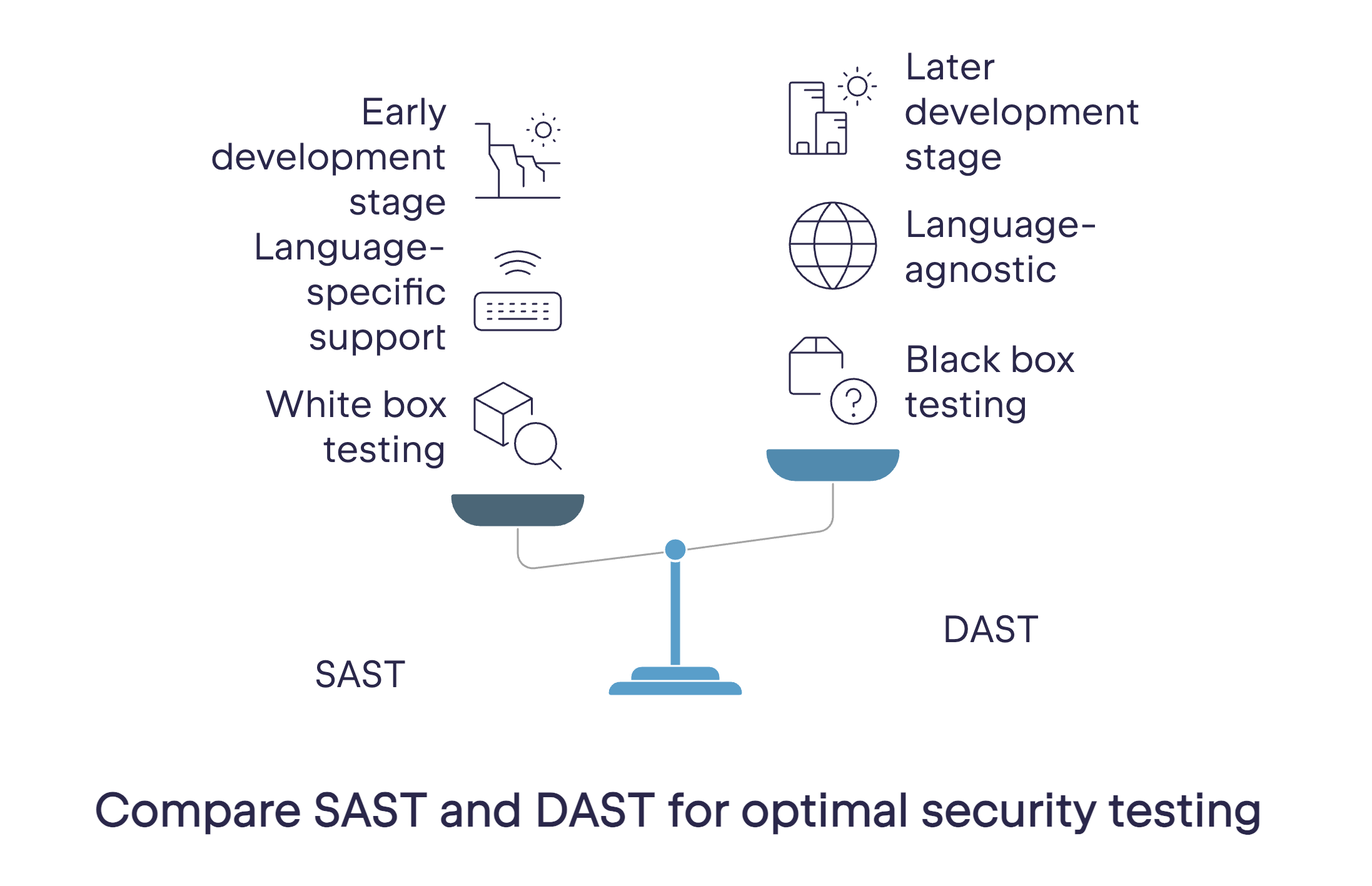
Testing approach
SAST is a type of white box testing. It examines the source code of your application for insecure coding patterns, such as improper input validation or hard-coded API keys.
Because SAST goes through your code line by line, it tests every possible branch, including any that may not be exposed at runtime and therefore caught by other forms of testing.
In comparison to SAST, DAST is a form of black box testing, meaning the tool has no access to the source code and instead evaluates your application from the outside. DAST tools simulate attacks, such as XSS, CSRF, and SQL injection, on running software.
Since DAST tests deployed applications, it can evaluate interactions with other systems and detect issues like credentials transmitted in plain text and security flaws arising from misconfigured servers or databases.
Usage
As SAST examines your source code, you need to find a tool that supports the programming languages and frameworks you’re using.
DAST, however, is language-agnostic. The only requirement for using DAST tools is that you build your application using web-based technologies.
Software development life cycle stage
With SAST, there’s no need to build or run your software before you can test it. This means you can run SAST scans early in the development process, such as before pushing your changes or when opening a pull/merge request.
You might also choose to schedule regular SAST scans of your entire codebase as part of a nightly test run, or each time you merge changes into a deployment branch.
DAST, on the other hand, requires an application to be deployed to a test environment. As a result, it can only provide feedback at a later point in the development process.
Although this creates a longer feedback loop, it also provides an opportunity to test interactions with other systems and verify the environment configuration.
Test results
SAST tools typically highlight the offending line of code in the test results. Some SAST tools also provide guidance on each vulnerability and how to remedy them.
As a black box testing technique, DAST tools aren’t able to identify the relevant line of code in test results. However, many DAST tools provide additional information about vulnerabilities and advice on how to address each issue.
Accuracy
Although both SAST and DAST carry the risk of false positives (i.e., incorrectly reporting a vulnerability), SAST tools tend to return more false positives because it examines the code out of context.
Comparing SAST and DAST
| SAST | DAST |
| White box testing – from inside out | Black box testing – from outside in |
| Analyzes the source code or static binaries for vulnerabilities | Looks for vulnerabilities while the application is running |
| Can be used on any type of software | Limited to web apps and services |
| Limited to the source code | Can test interactions with other services/APIs |
| Tests every branch of the code, including those not exposed at runtime | Mimics behavior of attackers and can identify environment/deployment specific issues |
| Pinpoints the line of code that introduces the vulnerability | Does not identify the source of the vulnerability in test results |
| Language and framework dependent | Language agnostic |
| Requires access to source code or binaries. Does not require a working build | Requires a working build and deployment to testing/pre-production environment |
| Ideal for use early in the CI/CD pipeline | Designed for use later in the CI/CD pipeline |
| Provides developers with immediate feedback on latest changes | Results provided later in the software development lifecycle |
When to use SAST, DAST, or both
A common misconception is that SAST replaces DAST, or vice versa. In fact, SAST and DAST are complementary testing techniques that are used at different points in the software development lifecycle. You can include both SAST and DAST in your CI/CD pipeline.
As SAST doesn’t require a running application, it’s ideal for use early on in the development process, enabling a “shift left” approach to security testing. You can use SAST tools, such as Checkmarx, Spectra, SonarQube, or Veracode, to verify your latest code changes haven’t introduced any new security issues.
By running a SAST scan as part of your early-stage automated tests (alongside linting and unit tests), you can address any new security issues before building other functionality on top. The earlier you run these tests and act on the results, the easier it is, as the changes will still be fresh in your mind.
🔧 SAST vs DAST tools: comparison table
| Tool | Type | Pros | Cons | Common use cases |
| SonarQube | SAST | – Open-source and enterprise versions – Integrates with many IDEs and CI tools – Customizable rulesets | – Limited to code-level analysis – May require tuning to reduce false positives | Early-stage code reviews, pre-commit checks in CI pipelines |
| Checkmarx | SAST | – Comprehensive security coverage IDE and CI/CD integration – Detailed remediation guidance | – Enterprise pricing – Initial configuration can be complex | Secure code analysis in large enterprises with compliance needs |
| Veracode | SAST | – Cloud-based with low setup overhead – Supports multiple languages | – Less control over scanning process – May have slower scan times | Enterprises looking for SaaS SAST with strong reporting features |
| Spectral | SAST | – Lightweight, fast scanning – Good for detecting hard-coded secrets | – Not as feature-rich as enterprise tools | Developer-first environments, secrets scanning |
| Burp Suite | DAST | – Manual and automated testing – Excellent for advanced security teams | – Steep learning curve – Limited CI/CD integration without extensions | Penetration testing, manual vulnerability verification |
| Acunetix | DAST | – Fast, automated scans – Great UI and reporting – API security testing | – False positives in some scenarios – Costly for smaller teams | Regular vulnerability scans in staging/pre-production environments |
| OWASP ZAP | DAST | – Free and open-source – Highly customizable | – Requires manual configuration – Not ideal for beginners | Lightweight DAST testing, educational or small-team environments |
| Invicti (Netsparker) | DAST | – Scalable and automated – Proof-based scanning to reduce false positives | – Enterprise-focused pricing – Less control over scan logic | Automated DAST in continuous deployment environments |
Once you merge your code changes, you can run additional automated SAST scans as part of your continuous integration (CI) flow. For instance, you might want to include a SAST tool in the automated tests you run after merging into specific branches, or as part of a nightly test run.
Again, this early feedback, combined with test results that identify the relevant code, supports a shift-left security approach and helps you address issues quickly.
Because DAST simulates attacks on a running application, it’s sometimes seen as a type of automated penetration testing. However, that doesn’t mean you should only use it when you’re running a pen test. Instead, as a type of automated security testing, DAST is ideal for use in an automated CI/CD pipeline.
As DAST requires a deployed application, the time from code change to test feedback is longer. Ideally, you should run DAST each time you deploy a build to a test environment. By incorporating a DAST tool like Acunetix, Burp Suite, or Invicti into your continuous delivery or continuous deployment process, you can detect security issues that SAST cannot identify.
That includes vulnerabilities resulting from changes to your environment configuration or from interactions with other services and APIs.
Using SAST and DAST (not SAST vs DAST!) in combination gives you the best of both worlds: early feedback that directs you to the source of the issue, plus verification your application as a whole can resist common attacks.
How to implement SAST and DAST effectively
To get the most out of your SAST and DAST tools, apply the following best practices:
- Do a baseline scan. If you haven’t used SAST or DAST on a project before, a good place to start is with a scan of your entire codebase and/or application to check for existing vulnerabilities.
- Prioritize your fixes. Both the baseline scan and subsequent test runs are likely to highlight a range of issues. Some will be more serious than others, so prioritize them accordingly. Once you’ve addressed the most important issues, you can start using SAST and DAST regularly to ensure you fix new issues as they emerge, while you continue to work through the backlog of minor issues.
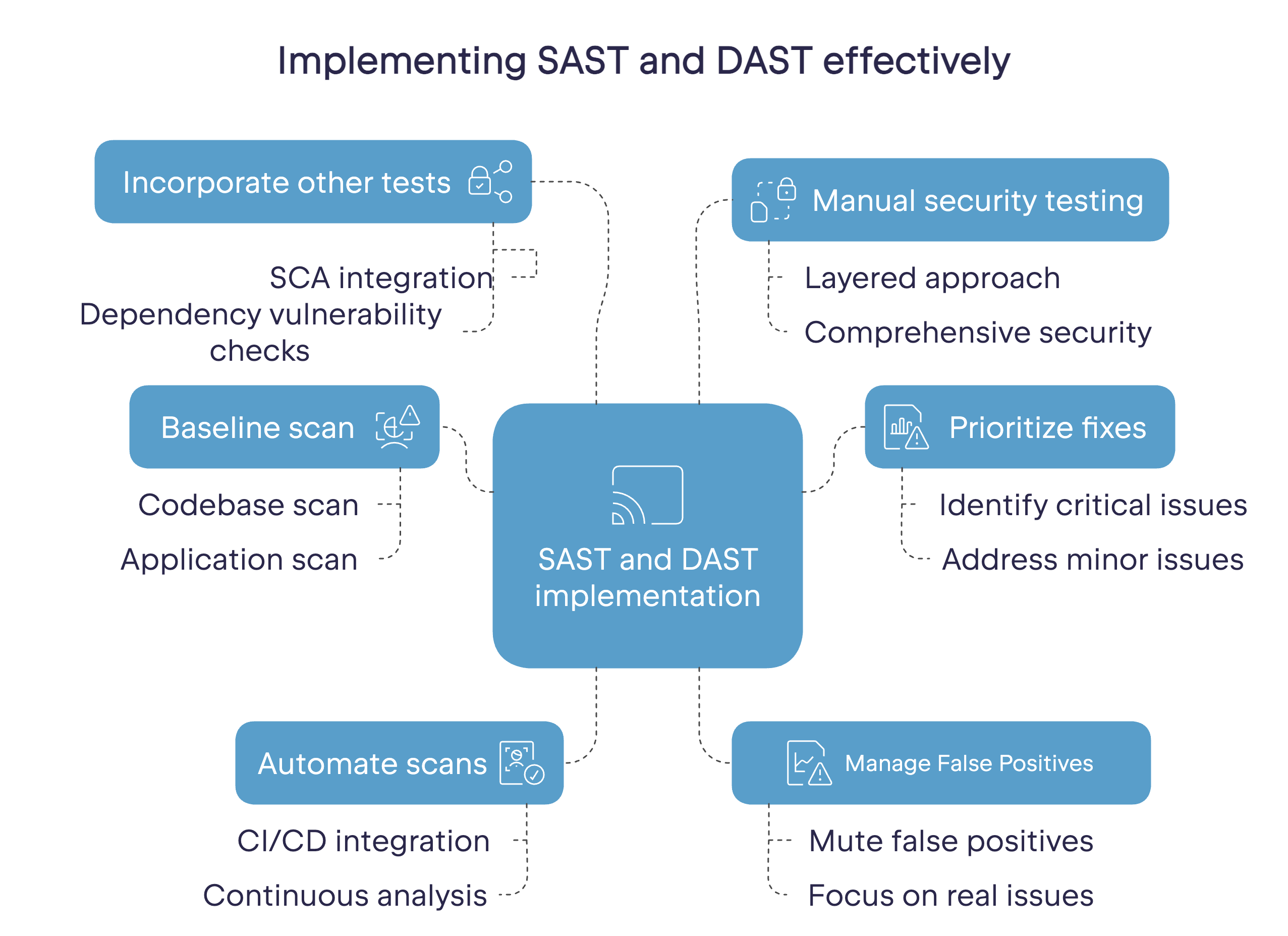
- Automate your SAST and DAST scans. Make continuous security testing part of your software development process. Incorporating SAST and DAST into a CI/CD pipeline helps shift security considerations further to the left (i.e., earlier in the process). Continuously analyzing and improving your software’s security posture is more effective and efficient than conducting quarterly security audits.
- Manage false positives. False positives can quickly become a distraction when reviewing security test results. Optimize the signal-to-noise ratio by choosing tools that let you mute false positives so you can focus on real issues.
- Incorporate other automated security tests in your pipeline. As SAST only checks your source code, consider pairing it with SCA (software composition analysis) to check your project’s dependencies for known vulnerabilities.
- Make time for manual security testing. Running SAST, DAST and other automated tests on every code change or build provides a degree of confidence in your software, but cybersecurity requires a layered approach.
How TeamCity can help
TeamCity is a CI/CD tool that enables software teams to automate their build, test, and deployment process, and get rapid feedback on their latest changes.
Extensive pipeline configuration options give you the flexibility to create CI/CD flows that suit your needs, including pre-tested commits, merge/pull request support, and scheduled builds.
TeamCity’s plugin support for a range of SAST and DAST tools – including Acunetix, Checkmarx, SonarQube, and Veracode – means you can easily incorporate automated security testing into your CI/CD process.
Each time a pipeline runs, on-the-fly test reporting alerts you to issues as they’re discovered, while detailed test reports help you get to the root cause quickly.
Key takeaways
- SAST and DAST are automated security testing techniques.
- Using these techniques can help you “shift security to the left”. This means you find and address security flaws earlier, thereby making the development process more effective and efficient.
- SAST checks your code line-by-line and is ideal for use early on in the development process.
- DAST simulates an attack on your running software and can only be used once your code has been built and deployed to a testing environment.
- Both SAST and DAST can be run as part of an automated CI/CD process.
- TeamCity is a CI/CD platform that supports a number of SAST and DAST tools alongside many other features designed to help you build secure and reliable software.
Subscribe to TeamCity Blog updates




