TeamCity
Powerful CI/CD for DevOps-centric teams
Building the Snyk Plugin for TeamCity
This guest blog post is brought to you by Brian Vermeer, Developer Advocate at Snyk.
 Snyk offers a developer-first solution for open source security. Snyk is developing a TeamCity plugin to help users with automated vulnerability scanning. Snyk’s blog post series documents their story of building the plugin to help others learn from their experience.
Snyk offers a developer-first solution for open source security. Snyk is developing a TeamCity plugin to help users with automated vulnerability scanning. Snyk’s blog post series documents their story of building the plugin to help others learn from their experience.In our previous post (Building open source security into the TeamCity flow with Snyk), we explained our motivation for building the Snyk plugin for TeamCity, and what we aim to achieve with it. As we explained, security is mainly used as a gating mechanism to make sure that whatever doesn’t measure up to policy doesn’t get shipped—but that isn’t always efficient. With Snyk’s plugin for TeamCity, we enable development teams to make the most of security analysis during the development stage, by helping to find and fix vulnerabilities with detailed and actionable insights.
In this follow-up post, we will highlight the Snyk features that we took advantage of when creating this plugin.
Taking advantage of the Snyk CLI
Finding and fixing vulnerabilities in your project’s dependencies is the core business of Snyk. With the Snyk CLI you can run scans on your projects from any machine—even your local development machine. The CLI automatically detects the type of project you have and creates a dependency tree. Snyk validates these dependencies against our proprietary vulnerability database. However, we do not only show whether a particular direct or transitive dependency contains a vulnerability, but also whether there is a possible solution.
For the TeamCity plugin, we use the same existing CLI capabilities to provide you these valuable insights.
We bundled the latest version of our CLI with the TeamCity plugin, which works by calling the CLI binary (embedded in the plugin) for scanning and then returning all key information in a structured JSON file. By default, we provide binaries for macOS, Linux, and Windows so, whatever system your TeamCity instance runs on, there is no need to separately download the Snyk CLI.
Additional capabilities: reporting and monitoring
To present this useful data in a report, we used yet another Snyk tool: the latest snyk-to-html binaries also ship with the plugin for macOS, Linux and Windows. Calling this tool with the Snyk CLI JSON output creates a fancy HTML report displaying all the insights you need to pinpoint and remediate vulnerable dependencies.
The Snyk CLI also enables monitoring your project from the Snyk interface: a snapshot of your dependency tree is uploaded to your Snyk account and then all your dependencies for that specific build are monitored on a regular basis. Additionally, you can enable active alerting (for example by email) so that every time a new vulnerability in your dependencies is found, you receive a notification. This monitoring capability is now also available in the TeamCity Plugin.
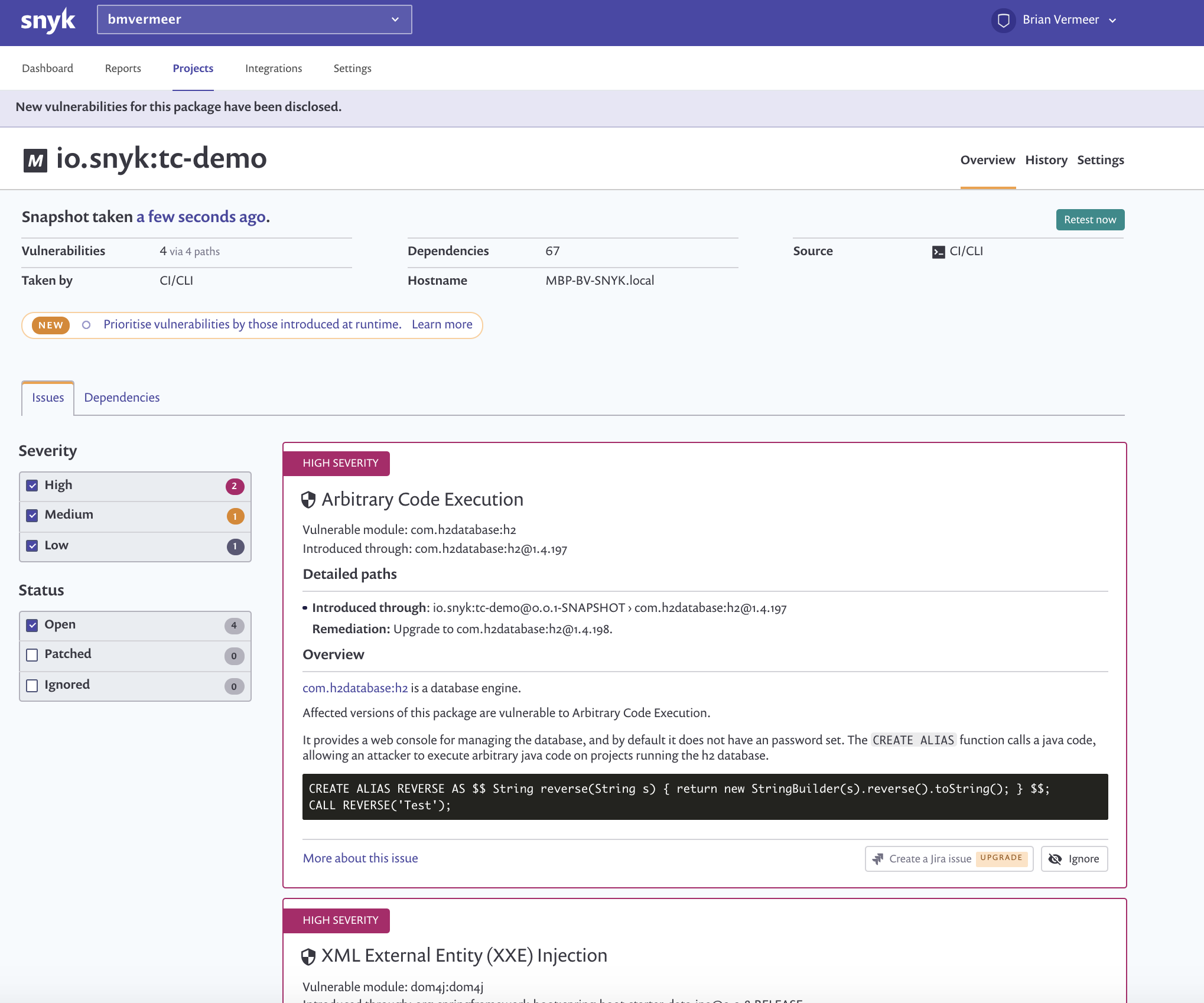
How we brought it all together
The plugin introduces a “Snyk Security” build runner, which can be added as a build step in TeamCity.
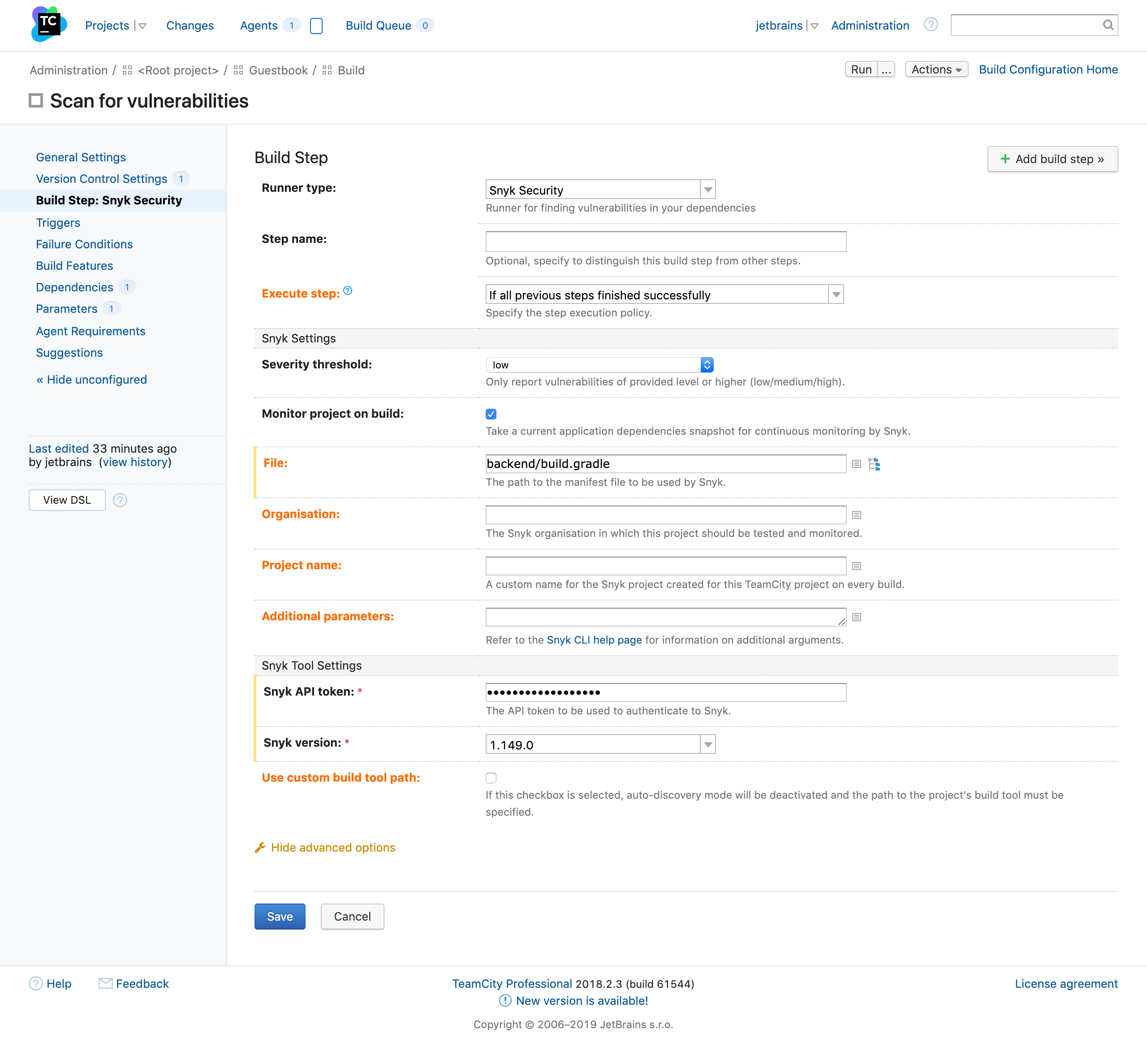
The new TeamCity plugin executes multiple commands and pushes the result forward. With the plugin, users can run snyk test and snyk monitor, ultimately, pushing the test output to snyk-to-html.
We implemented this in the build agent part of the plugin by using a MultiCommandBuildSessionFactory to chain all these commands to the shipped binaries. If everything succeeds then an HTML artifact is produced, which we then made available to the user. The plugin adds the “Snyk Security Report” tab to a finished build page.
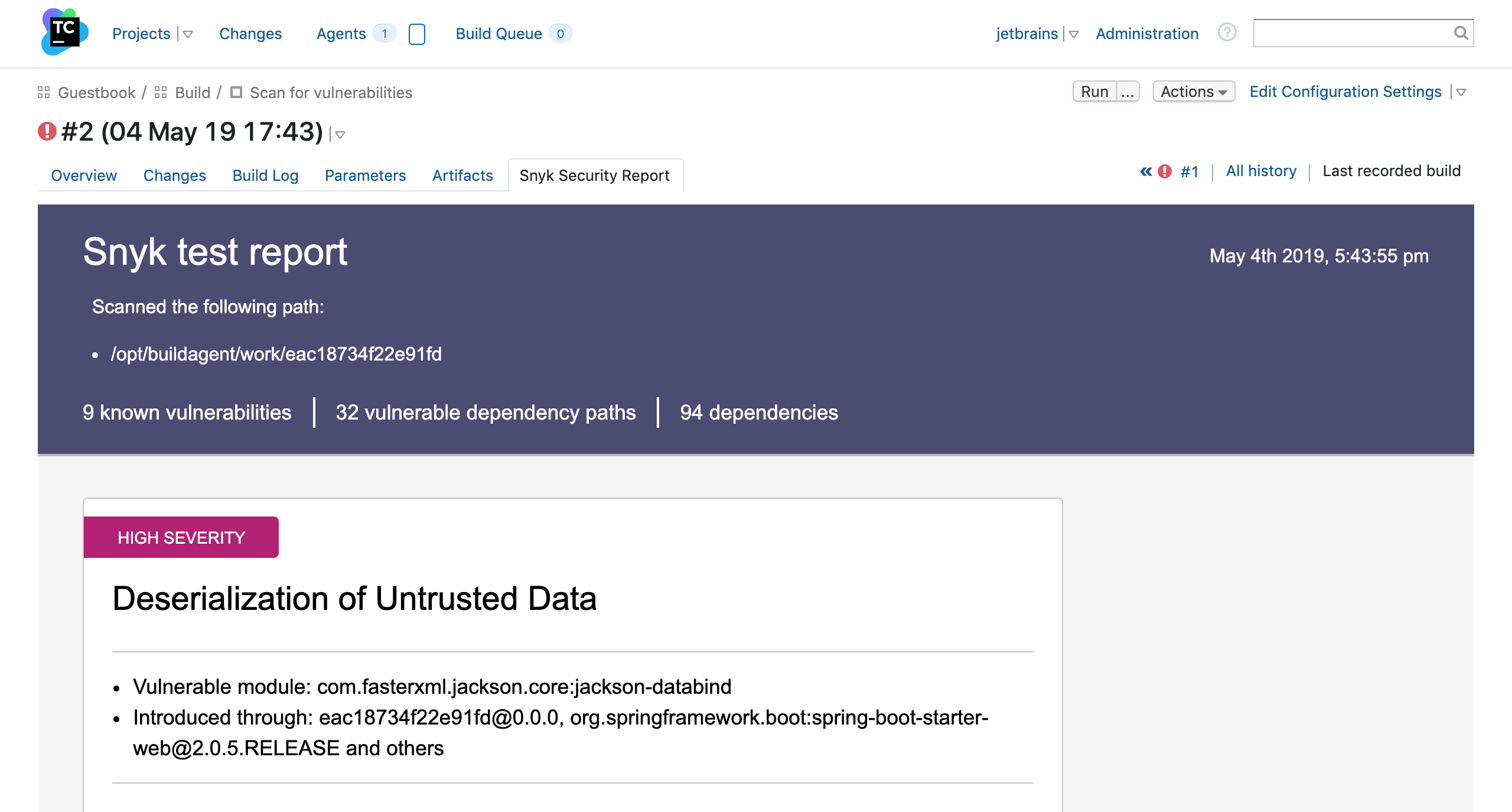
A good way to use this step is to run it before deployment and add a snapshot dependency from the deployment build configuration to a configuration which contains the Snyk Security step. You can set it up in a way that if a security scan does not pass a specified threshold, the deployment won’t be started.
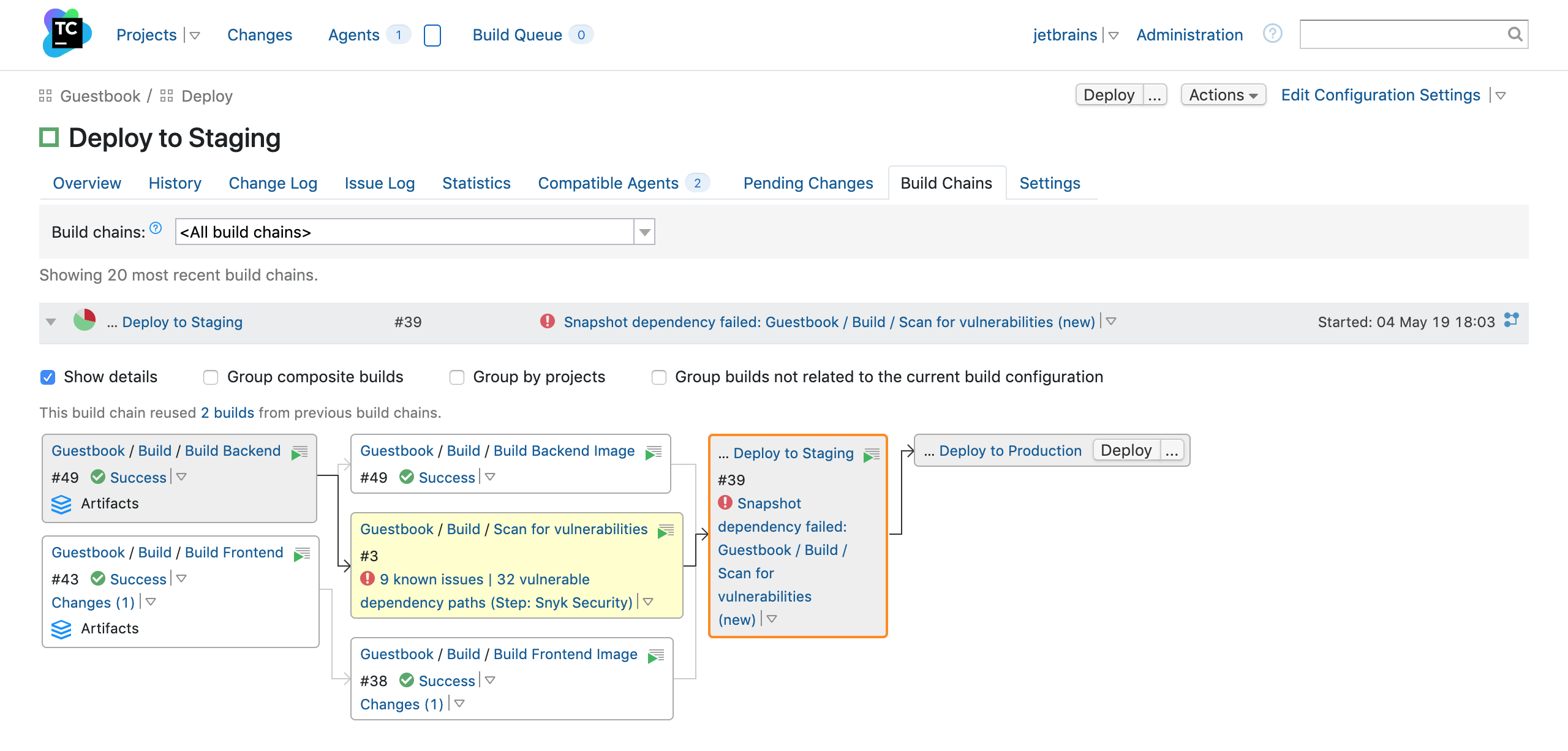
Once you fix all the vulnerabilities with the remediation advice that Snyk provides in the report, you are good to go. Make sure that before deploying to production you run a test including snyk monitor. That way, when you ship and deploy that artifact, Snyk continues to monitor it as long as it is in production, and alerts you if new vulnerabilities are found in that build.
Happy coding!
Subscribe to TeamCity Blog updates








