TeamCity
Powerful CI/CD for DevOps-centric teams
What Is SAST? A Guide to Static Application Security Testing
This article is brought to you by Thinus Swart, draft.dev.
Static application security testing (SAST) is a method for identifying vulnerabilities in application source code, binaries, or bytecode early in the software development lifecycle (SDLC). By analyzing code before it’s compiled or run, SAST allows developers to catch potential security flaws before they can be exploited in production.
With cybersecurity threats on the rise, companies without SAST are at risk of significant financial and reputational damage if their applications or systems are breached. According to IBM’s Cost of a Data Breach Report 2024, the global average cost of a data breach is USD 4.88 million.
Integrating SAST into the SDLC aligns with the shift-left approach that’s being embraced by modern development teams. Shifting left involves addressing code security and code quality concerns much earlier in the development process, rather than when the project has already gone live. It embraces a proactive approach to code and application security that can also lead to better code quality and a faster time to market.
In this article, we’ll explore:
- Why SAST matters
- Key considerations when choosing an SAST tool
- Best practices when implementing an SAST tool
What is SAST and why does it matter?
SAST is a code analysis method that checks an application’s source code without running it. It helps find security issues like SQL injection, cross-site scripting (XSS), and buffer overflows by analyzing the code’s structure and logic during development. This allows developers to fix problems early, reducing security risks.
Unlike reactive security measures that address vulnerabilities after an attack or late in the development cycle, SAST takes a proactive approach. By integrating automated scans into CI/CD pipelines using tools like SonarQube or Snyk, teams can continuously validate security and minimize the attack surface from the outset.
? Read our Building the Snyk Plugin for TeamCity blog post for more information about how this works in TeamCity.
The early detection of security vulnerabilities minimizes the risk of costly incidents, data breaches, and compliance violations, while protecting against reputational damage, which can be difficult to recover from.
SAST not only strengthens your application’s security but also helps your organization avoid fines and legal risks from noncompliance by:
- Complying with regulatory standards: SAST helps organizations meet regulatory standards by identifying security vulnerabilities that could impact customer data protection.
For example, it supports compliance with the General Data Protection Regulation (GDPR) for data privacy in Europe and HIPAA for safeguarding medical health information in the US. By proactively addressing security risks in code, SAST can help you avoid hefty fines for noncompliance with these regulations. - Aligning with OWASP best practices: The OWASP Top Ten is a widely recognized standard for identifying the most critical web application security risks. Following OWASP guidelines helps developers write more secure code and mitigate common vulnerabilities that attackers frequently exploit.
Many SAST tools are designed to detect OWASP Top Ten issues, making compliance with these best practices easier.
- Mitigating the risk of financial and reputational damage: SAST’s early identification of code vulnerabilities can help mitigate the risk of cybersecurity breaches, which are costly both in monetary terms and in potential damage to brand reputation and customer trust. The average cost of a data breach has risen to millions of dollars, with the added risk of losing customer loyalty and investor confidence.
Key considerations when choosing an SAST tool
Selecting the right SAST tool is crucial to your SDLC. Not all tools are created equal, and choosing one that aligns with your team’s needs can significantly increase adoption and usage.
Key factors like language support, detection accuracy, and seamless integration into your CI/CD pipelines should guide your decision-making.
Language coverage
One of the more important things to consider is the language and framework support a potential SAST tool can offer. A few basic steps can significantly help when deciding on an SAST tool:
- Inventory your codebases: Begin by cataloging the programming languages, frameworks, and libraries currently in use across your projects. Consider legacy applications and codebases as well, since these applications might not have had a code security review in the past and could benefit from the use of an SAST tool.
- Anticipate future needs: Consider upcoming projects or new clients that might require the adoption of different languages or frameworks.
An SAST tool with broad language coverage would be advantageous if your projects span different languages. Conversely, if your organization specializes in a specific language, it might be best to look for an SAST tool that specializes in it as well. - Evaluate framework-specific support: Many modern applications rely heavily on frameworks like Django for Python or React for JavaScript. While these frameworks usually do a good job of minimizing developer error, introducing misconfiguration issues can be easy. An SAST tool that covers a specific framework would be able to pick up these misconfigurations and insecure patterns.
By following these steps, you can ensure your chosen SAST tool provides comprehensive language and framework coverage and reduces the risk of missed vulnerabilities in critical parts of the application.
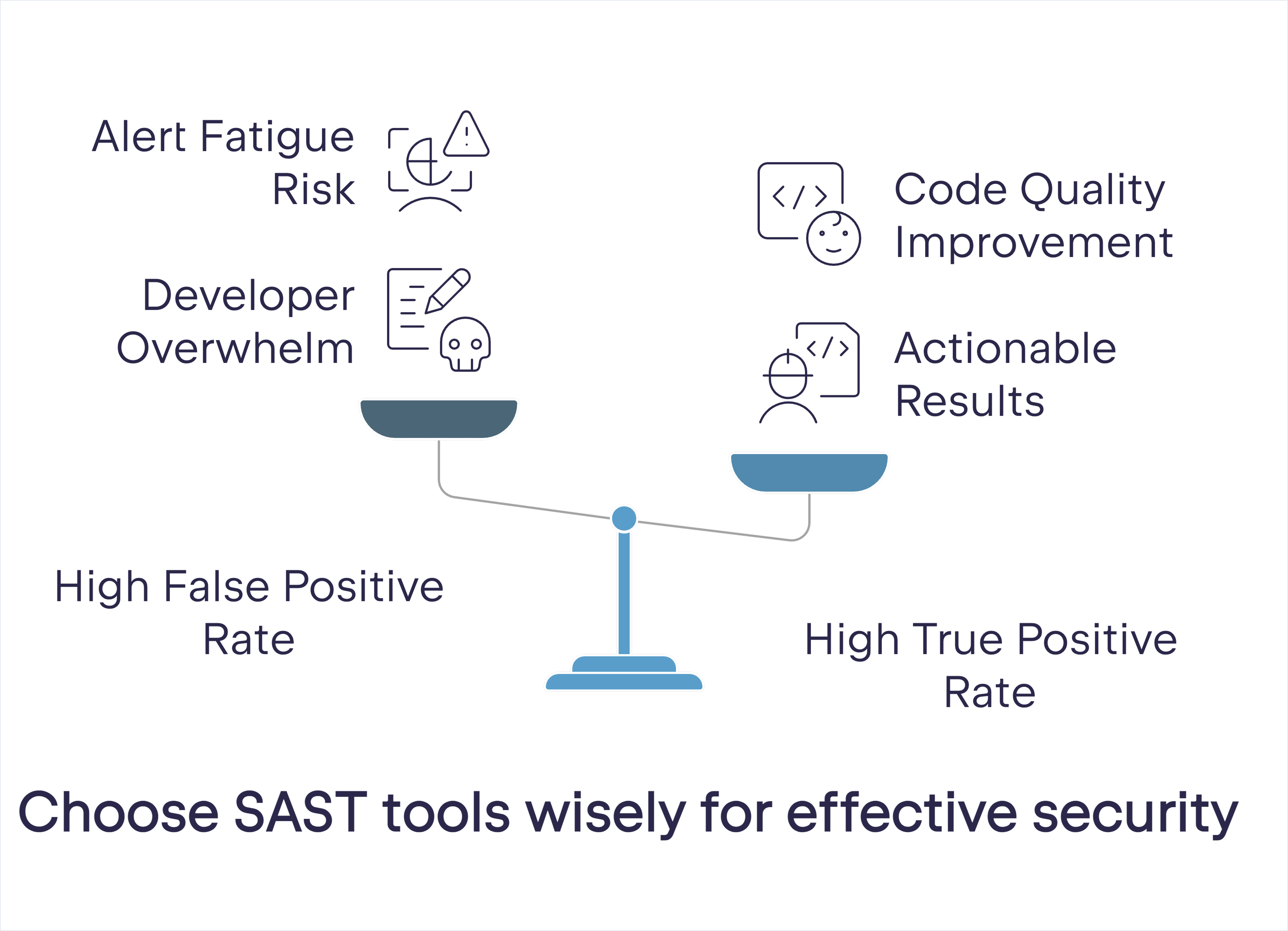
Low false positive rate/high true positive rate
Detection accuracy is a very important factor when selecting an SAST tool for your organization. Tools with high false positive rates can overwhelm developers and increase the time to release, as they end up chasing nonexistent or trivial issues.
This high false positive rate can also lead to alert fatigue, which in turn can lead to noncompliance. Conversely, a tool with a high true positive rate provides actionable results, helping developers focus on real security risks.
While you can use sample reports and benchmarks to measure the accuracy of these tools, doing so doesn’t replace the experience of conducting a trial run of an SAST tool you’re considering on your existing code.
Pay attention to how well the tool distinguishes between actual vulnerabilities and benign code patterns. Tools that provide good remedies for each finding can further improve code quality by reducing the guesswork for developers.
It’s also strongly recommended to look for tools that allow you to customize and fine-tune detection rule sets to better fit your projects. For example, you might want to suppress specific warning messages due to customer limitations that you have to work around.
The flexibility to fine-tune your scanning parameters can help further improve the signal-to-noise ratio, making it easier for developers to focus on real security issues and integrate security checks into their workflow.
Ease of integration into CI/CD pipelines
To make the most effective use of an SAST tool, you need to scan early and scan often. Automating your security checks is key to enabling your developers to fix issues as early as possible in the development lifecycle.
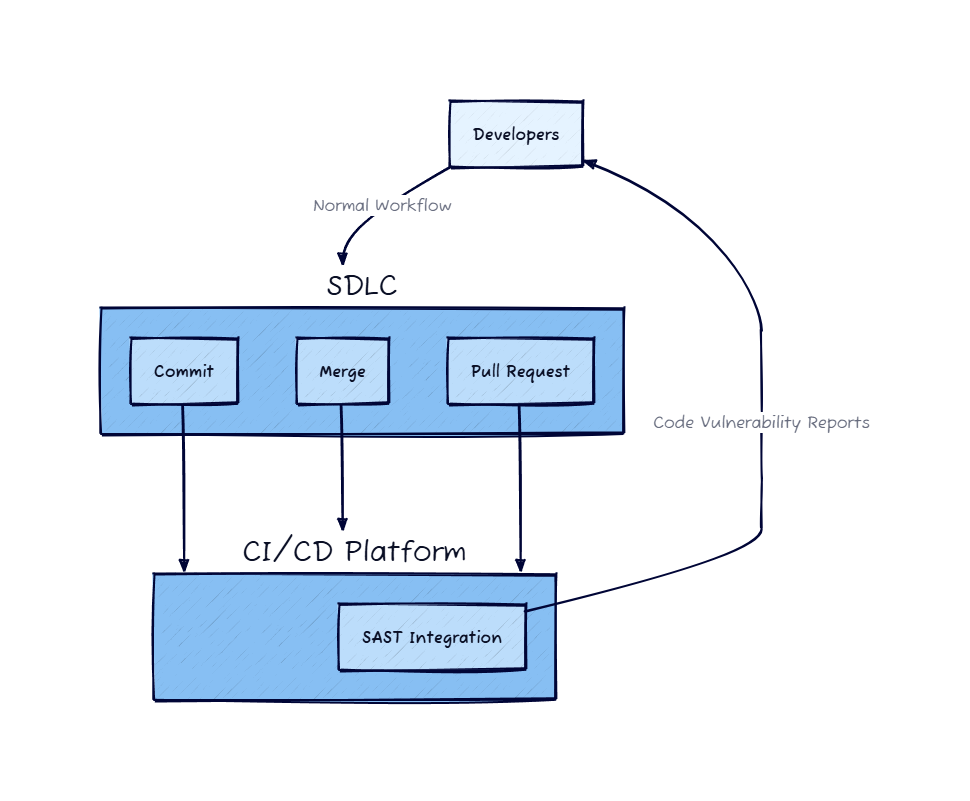
Any SAST tool that can integrate with a CI/CD platform like JetBrains TeamCity will allow you to automate your security checks at important phases in the development cycle – for example, every time a new branch needs to be merged into the main branch or a pull request is submitted for a software patch.
This can supply developers with feedback directly within the workflow they’re used to, and they can respond to vulnerabilities immediately.
Best practices when implementing an SAST tool
While integrating an SAST tool into your development process is an important step, ensuring it’s configured properly and used effectively further enhances your developers’ experience. This can foster a culture of being vigilant and employing secure coding practices as early as possible.
For this to happen, keep these best practices in mind when advocating for and deploying an SAST tool in your environment.
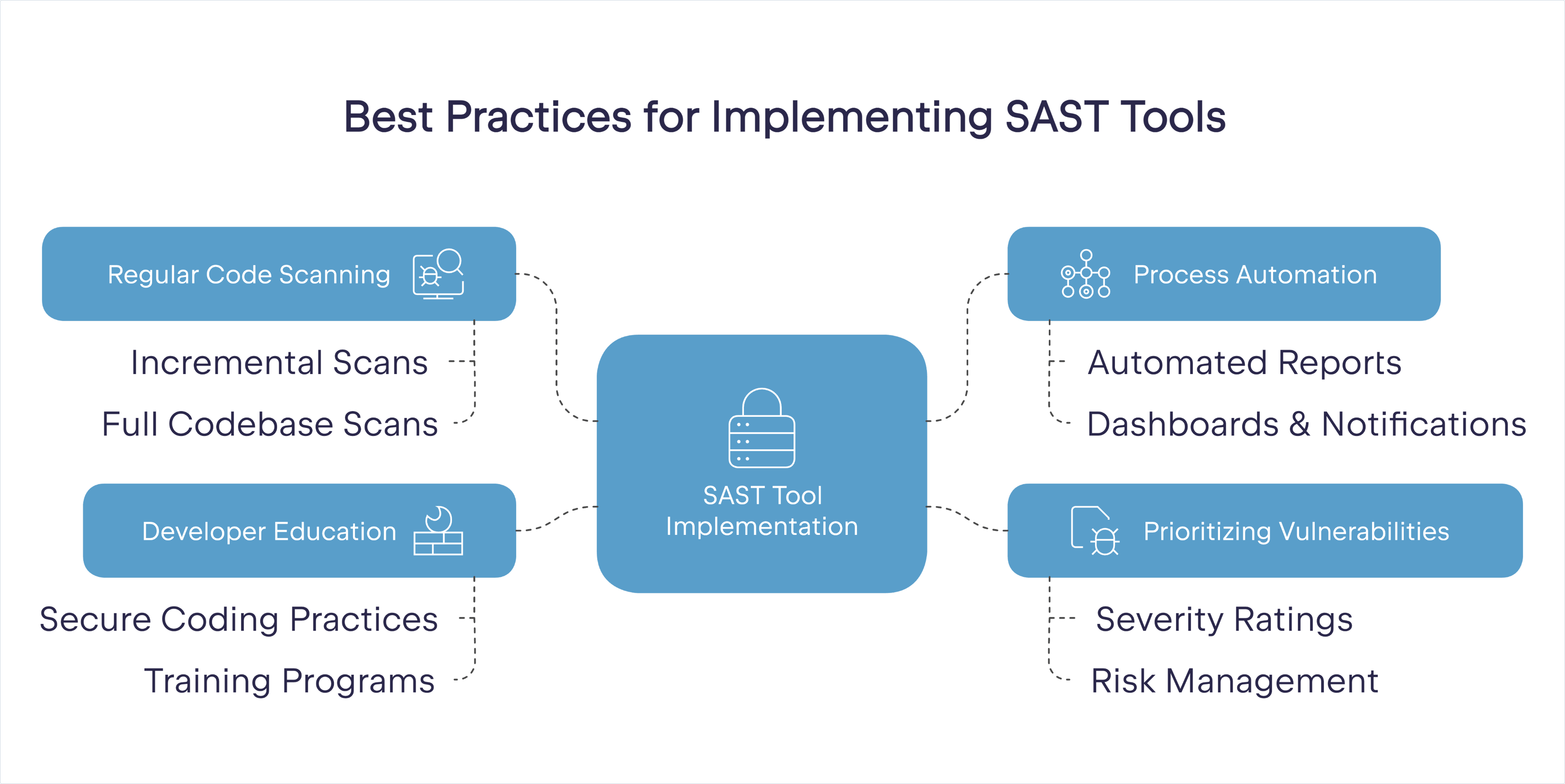
Scan your codebase regularly
Regular scanning is key to identifying vulnerabilities as they occur. Automating your scanning at different stages of the development lifecycle allows you to catch and remediate issues before the code gets put into production.
While incremental scans of commits and pull requests are a great idea, you should also schedule full scans of the entire code repository at regular intervals. Full scans can reveal vulnerabilities in legacy code or parts of the application that are rarely accessed and that wouldn’t show up in a pull request or code commit.
Automate as much of the process as possible
A lot of what has been discussed so far, like full codebase scans and CI/CD integration, only makes sense once you make the move to automating as much of the process as possible. As previously discussed, automation is key to driving the adoption of an SAST tool, as it provides your developers with immediate feedback that they can act upon.
In addition to automating scans, you can automate monthly reports or implement dashboards or notification systems to help your team monitor and track their code quality trends over time.
Prioritize critical vulnerabilities
Not all vulnerabilities carry the same level of risk, and teams must focus their efforts on the critical ones first. SAST tools generally supply a severity rating for vulnerabilities that have been identified. This severity rating should align with your organization’s risk management strategies and help you decide which vulnerabilities to prioritize. Issues that could lead to data breaches or significant system compromise should be addressed immediately, while less pressing ones can be addressed during regular patching schedules.
Educate developers about secure programming practices
Even the best SAST tool is only as effective as the team using it. Developers must understand how to interpret scan results and recognize how adopting secure coding practices can help speed up the development process for the entire team. If the SAST tool you’re adopting offers training, you should invest in that training for your developers to familiarize them with the tool’s interface, features, and reporting capabilities.
Work on fostering a security-first mindset in your development team and the team culture in general. Encourage collaboration between your security and your development teams, and emphasize that security is a shared responsibility across the entire organization.
Conclusion
Static application security testing is an essential component of a secure software development lifecycle. In this article, we explored what SAST is, why it matters, and the key considerations for selecting the right SAST tool for your organization.
We also identified some best practices to optimize SAST implementation and ensure that security scans are both effective and automated. If you implement SAST correctly, your teams will be able to identify vulnerabilities earlier in the development lifecycle, reduce risks in general, and ensure compliance with industry standards.To streamline your SAST implementation efforts, consider integrating it with a CI/CD platform like JetBrains TeamCity, which offers support for many SAST tools and SAST providers via its plugin marketplace.
Subscribe to TeamCity Blog updates






